First field test of encrypted chat over HF radio. Georgia to Michigan, VARA HF in 2300 Hz wideband mode, Reticulum handling Curve25519 key exchange and AES-256-GCM encryption with forward secrecy. The link held for 24 minutes through SNR as low as -17.1 dB. Zero errors. Clean disconnect.
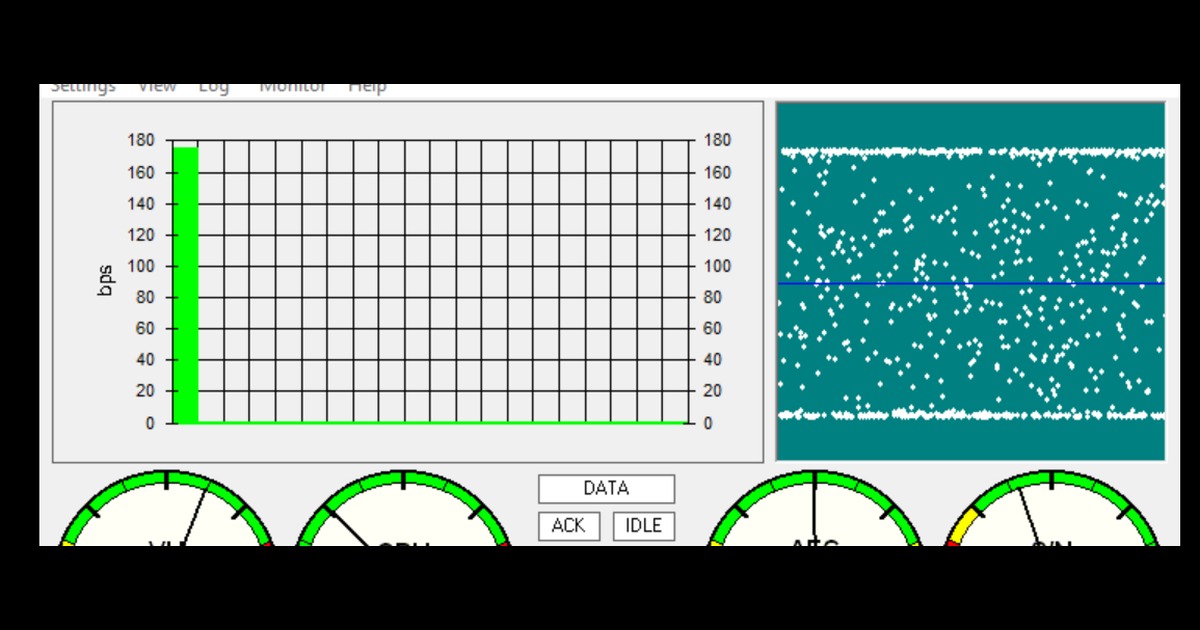
The signal degraded throughout the session. Early readings averaged +3.3 dB. The final third averaged -7.0 dB. VARA spent 56% of the session at its minimum speed level: 18 bps, roughly five characters per minute. The link never dropped.
The overhead problem:
Only 23% of transmitted bytes were actual chat text. The rest was security packaging. Type “test” (4 characters) and the system sends 102 bytes over the air. The fixed per-message cost breaks down like this:
| Component | Bytes |
|---|---|
| AES-256 IV + HMAC | 48 |
| X25519 ephemeral key (forward secrecy) | 32 |
| RNS packet header | 20 |
| RNS channel envelope | 6 |
| AES block padding | 1-16 |
| KISS framing | 3 |
| Fixed overhead per message | ~110 |
At 18 bps, those 110 bytes cost 49 seconds of airtime before a single character of text goes out. A max-length 408-character message is 10x more efficient than a 4-character message. Every message pays the same tax.
Why 500 Hz mode changes everything:
The 2300 Hz mode spreads power across 52 carriers. At -3 dB SNR average, each carrier got almost nothing. 500 Hz mode concentrates the same power into 2 carriers. Under these conditions, 500 Hz would have sustained 88-177 bps (SL4-SL5) instead of 18 bps (SL1). Same radio, same power, same path.
| Metric | Value |
|---|---|
| Path | Georgia to Michigan (HF SSB) |
| Session duration | 24 min 26 sec |
| VARA bandwidth | 2300 Hz |
| Encryption | AES-256-GCM + Curve25519 + forward secrecy |
| Total transfer | 3,646 bytes (1,886 TX / 1,760 RX) |
| Chat text efficiency | 23% of bytes |
| SNR range | -17.1 to +10.6 dB (avg -3.1) |
| PTT cycles | 231 |
| TX duty cycle | 51.4% |
| Errors | 0 |